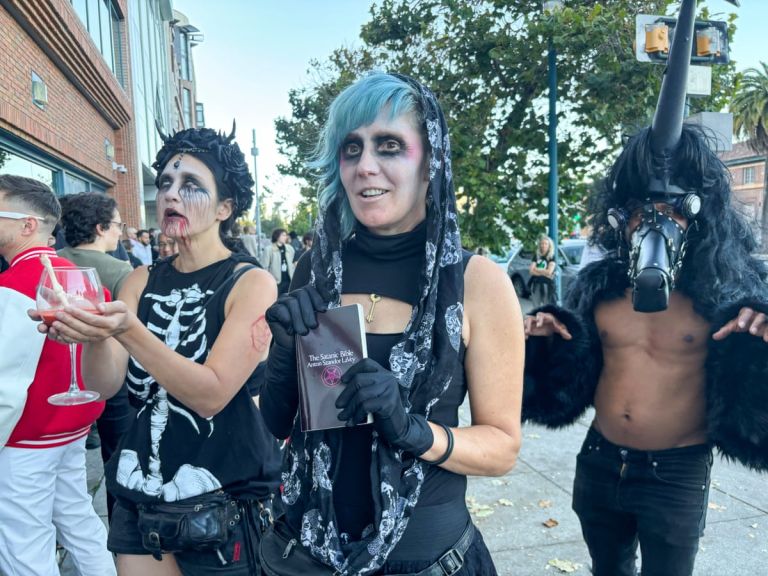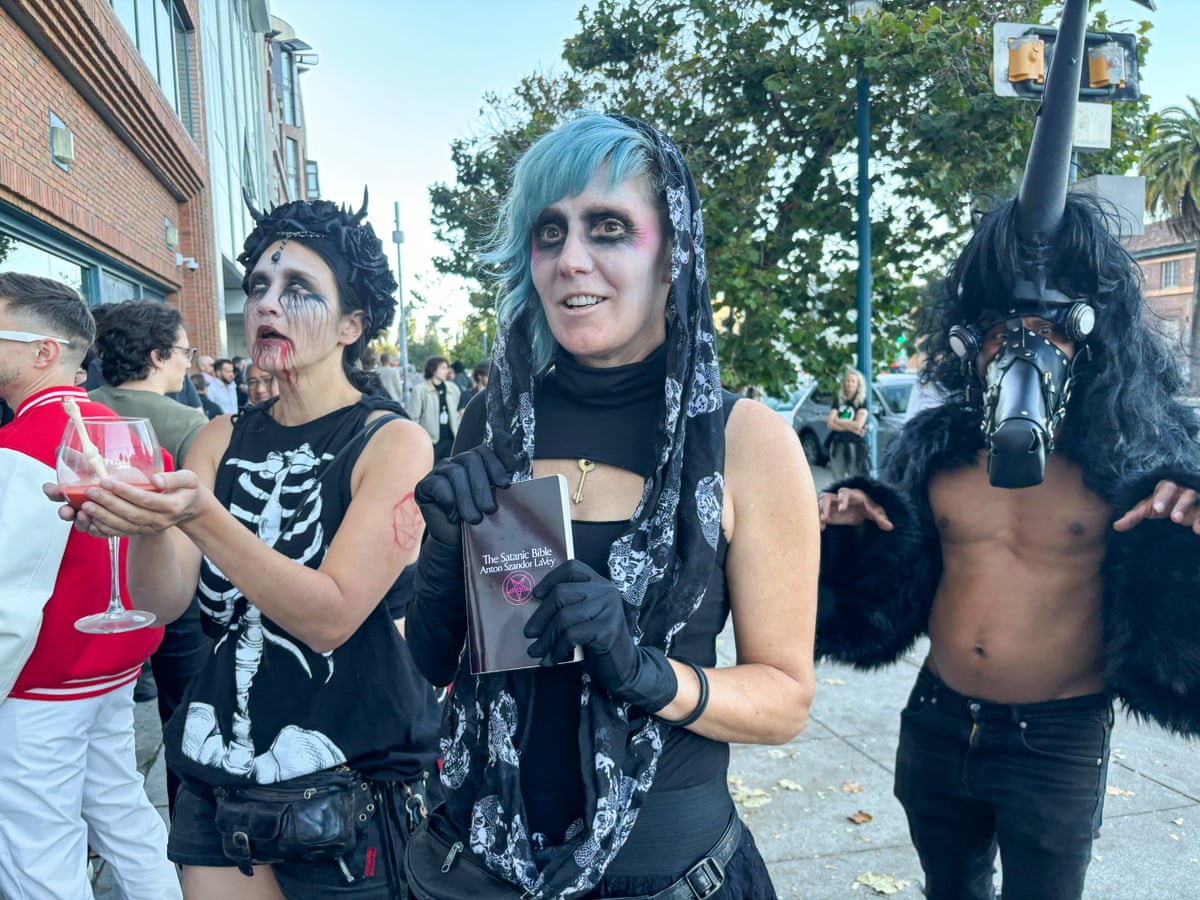I was trading New Year’s resolutions with a circle of friends a few weeks ago, and someone mentioned a big one: sleeping better. I’m a visual neuroscientist by training, so whenever the topic pops up it inevitably leads to talking about the dreaded blue light from monitors, blue light filters, and whether they do anything. My short answer is no, blue light filters don’t work, but there are many more useful things that someone can do to control their light intake to improve their sleep—and minimize jet lag when they’re traveling.
My longer answer is usually a half-hour rant about why they don’t work, covering everything from a tiny nucleus of cells above the optic chiasm, to people living in caves without direct access to sunlight, to neuropeptides, the different cones, how monitors work, gamma curves, what I learned running ismy.blue, corn bulbs, melatonin, finally sharing my Apple Watch & WHOOP stats. What follows is slightly more than you needed to know about blue light filters and more effective ways to control your circadian rhythm. Spoiler: the real lever is total luminance, not color.
↫ Patrick Mineault
And yet, despite a complete and utter lack of evidence blue-light filters do anything at all, even the largest technology companies in the world peddle them without so much as blinking an eye. It’s pure quackery, and as always, we let them get away with it.
Peter Thiel is worried about the antichrist. It could be the US. It could be Greta Thunberg. [...]
On the day of Thiel's final lecture in San Francisco, as the mostly young and mostly male crowd lined up to get in, a group of about 20 protesters stood out front holding anti-Palantir and anti-Ice signs that said things such as "Predatory tech", "We do not profit from people who profit from misery" and "Not today Satan".
A trio of self-described "satanists" dressed in black costumes with goth makeup walked up and down the line of attenders carrying a goblet of red liquid with a small plastic replica of a bone. "Will you bring our dark lord Peter Thiel this baby's blood?" they asked. Then they performed what they called a "dark ritual", dancing slowly in a circle to Mozart's Requiem in D minor, which ended with them writhing on the city sidewalk, and yelling: "Take us to your personal hell ... Thank you for being our dark lord." [...]
Thiel said that international financial bodies, which make it more difficult for people to shelter their wealth in tax havens, are one sign the antichrist may be amassing power and hastening Armageddon, saying: "It's become quite difficult to hide one's money."
I am constantly re-discovering that billionaires are some of the dumbest motherfuckers on the planet.
With a new majority on the Board of Supervisors, along with control over the Mayor's and District Attorney's Offices, the school board, and the local Democratic County Central Committee, political power in San Francisco has been consolidated in the hands of so-called "moderates" funded by and friendly to the interests of the tech and real estate industries. Put in the language of our political moment, San Francisco's halls of power are awash with Abundance. Not coincidentally, San Franciscans are suffering more than ever in just about every measurable way, and City Hall is simply ignoring their plight. [...]
San Franciscans are highly preoccupied with Trump's shocking and constant attacks on democracy, ICE raids disappearing of our neighbors, and exacerbation of the two-year-long genocide in Gaza. Mayor Lurie barely acknowledges these issues. In contrast to big city mayors like Boston Mayor Michelle Wu, Oakland Mayor Barbara Lee, and Chicago Mayor Brandon Johnson, Lurie refuses to take a stand against ICE kidnappings and his police department won't even protect those who do. Outrageously, SFPD's stated position is that its priority is to protect ICE agents from protestors.
This is a stunning lack of leadership for a Democratic mayor in a sanctuary city widely considered to be the nation's progressive heartland, at the precise moment when American fascism begs confrontation. But even more squarely on the plate of San Francisco's current leaders is the fact that local economic conditions have rapidly deteriorated for the city's working people and poor in the short time since they came into power.
Today, it comprises 69% of my total URLs served. (Nice.)
Normally it feeds junk after a few seconds delay, but in "high-load mode" it bans IPs for 30 days instead. High-load mode is entered when the free-worker count is low, and ends when it has been calm for 15 minutes.
This month it has been in high-load mode 50% of the time: 15 out of 30 days of traffic.
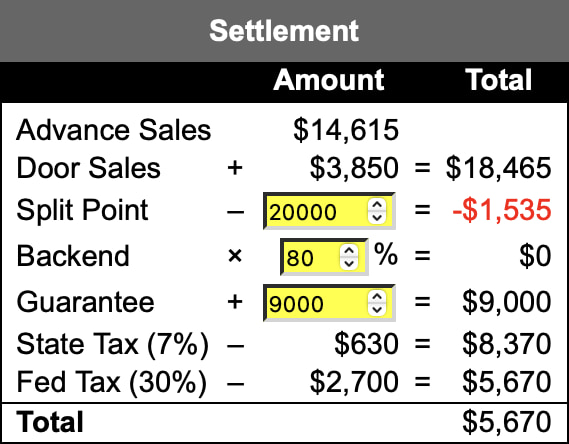
It is a small and self-contained PHP and JavaScript library for generating HTML tables of spreadsheet-like reports, including arithmetically-computed cell values.
I did this while refactoring some of DNA Lounge's internal business systems to have simpler code and less duplicated logic. This let me delete so much code!
But it took me a while to actually bite the bullet and do it. "I am not going to write a spreadsheet", I kept saying to myself, "that's stupid."
"Ok, maybe just a little bit of a spreadsheet. This far no farther."
"Ok, maybe just a little bit more."
As the Big Black song says, "I tell myself I will not go, even as a drive there."